Raspberry Pi based prototypes

Integrating an RFID Reader with a Raspberry-Pi
At Openest, we often build rapid prototypes by combining off-the-shelf solutions to meet startup needs. To expand our toolkit, we added a simple RFID module
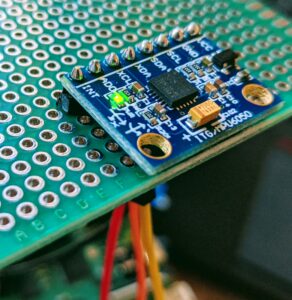
Use the MPU6050 accelerometer on Raspberry-Pi
Here’s how to use the MPU6050 on Raspberry-Pi or any embedded Linux system. The MPU-6050 & MPU-6000 are interesting components from Invensense. They include an

How to activate Raspberry-pi’s i2c bus
I recently completed the Proof of Concept for a client project using embedded Linux. In this context, I used the I2C bus of my new
Raspberry Pi based prototypes

MQTTS : How to use MQTT with TLS?
In a previous article we presented how the MQTT protocol works. Here we use its secure variant: MQTTS. It is a good practice to use
Board Support Package for Linux
Board Support Package for demo boards When developing an embedded system, you will be attracted by new system on chip (SoC) with functionality that can

MQTT a protocol for your connected embedded systems
There are many MQTT clients and servers in different languages and operating systems: it is an excellent solution for connected embedded systems. And of course,
